This blog discusses how you can manage and maintain granular level permissions across multiple AWS accounts with no extra cost, automation and Infra-as-Code approach.
Nowadays, every organization prefers to have separate AWS accounts so that they could allow teams to have full privileges and flexibility to work. This helps increase the efficiency of the team without worrying about segregating their infrastructure from other teams.
Managing AWS accounts using AWS organization help in many ways:
- Centralized account and identity management
- Centralized IAM policies and roles management
- Separate billing costs per account/team
- Compliance friendly, etc.
An organization owning 10-100 accounts makes it difficult to maintain granular level permissions for users across all account/teams/environment.
To understand and develop an easier way to manage all account properly let’s take a scenario.
In Company LEARNAWS teams have their own dedicated AWS accounts. Since the number of teams is growing they would want to manage all the accounts centrally including giving minimum permissions on production accounts.
Organization structure for LEARNAWS company looks something like this:
- It has 4 teams IT, CRM, BI and Marketing
- Each team uses 3-4 AWS sub-accounts to divide its infrastructure according to Development, Staging and Production environment
The team of Operations engineers have been tasked to design a solution which centralizes everything and is automated.
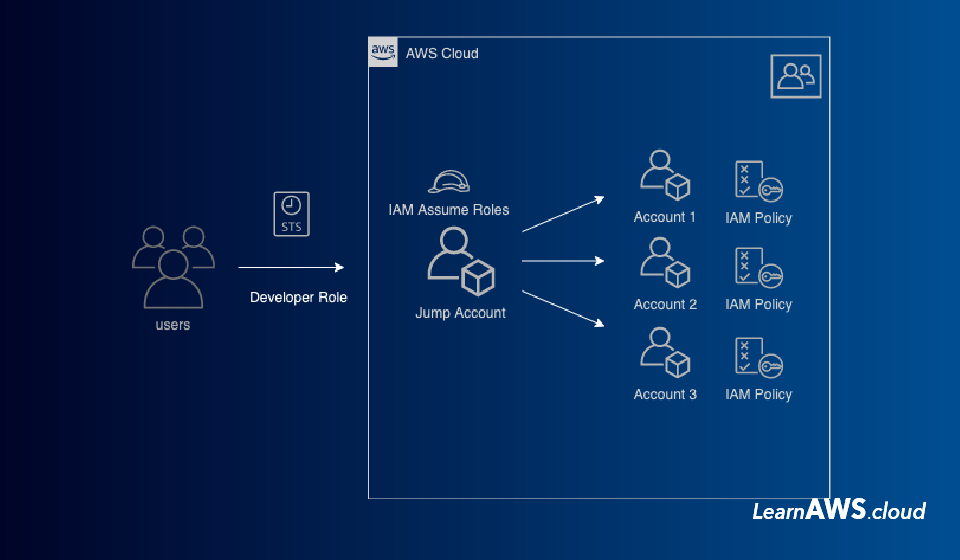
The Operations team decided to move each account under one AWS organization and came up with a plan to control IAM user access using a Jump/Identity Account.
A Jump/Identity Account will authenticate and authorize every employee and allow usage IAM Assume Role to get access to their team accounts.
To incorporate this type of User access management we will use the following AWS services:
- IAM – User, Roles and Groups
- AWS CloudFormation
- AWS Code Pipeline
Architecture for the same should be:
Here are sample code and repository structure for setting up a centralized authorization and authentication approach for the accounts under an organization:
https://github.com/bhargavamin/iam-access-multi-account-architecture
I hope this article helped you!
Ref:
https://d0.awsstatic.com/whitepapers/Security/AWS_Security_Best_Practices.pdf
https://aws.amazon.com/blogs/security/iam-share-aws-resources-groups-aws-accounts-aws-organizations/
Feel free to share your thoughts in comments below.